
All You Need to Know About Wireless Headsets
The wireless headphone is a device that receives sounds from a source using wave technology. The most suitable model is selected depending on the operating conditions. Many people believe that the….
A wonderful serenity has taken possession of my entire soul, like these sweet mornings of spring which I enjoy with my whole heart.

The wireless headphone is a device that receives sounds from a source using wave technology. The most suitable model is selected depending on the operating conditions. Many people believe that the….
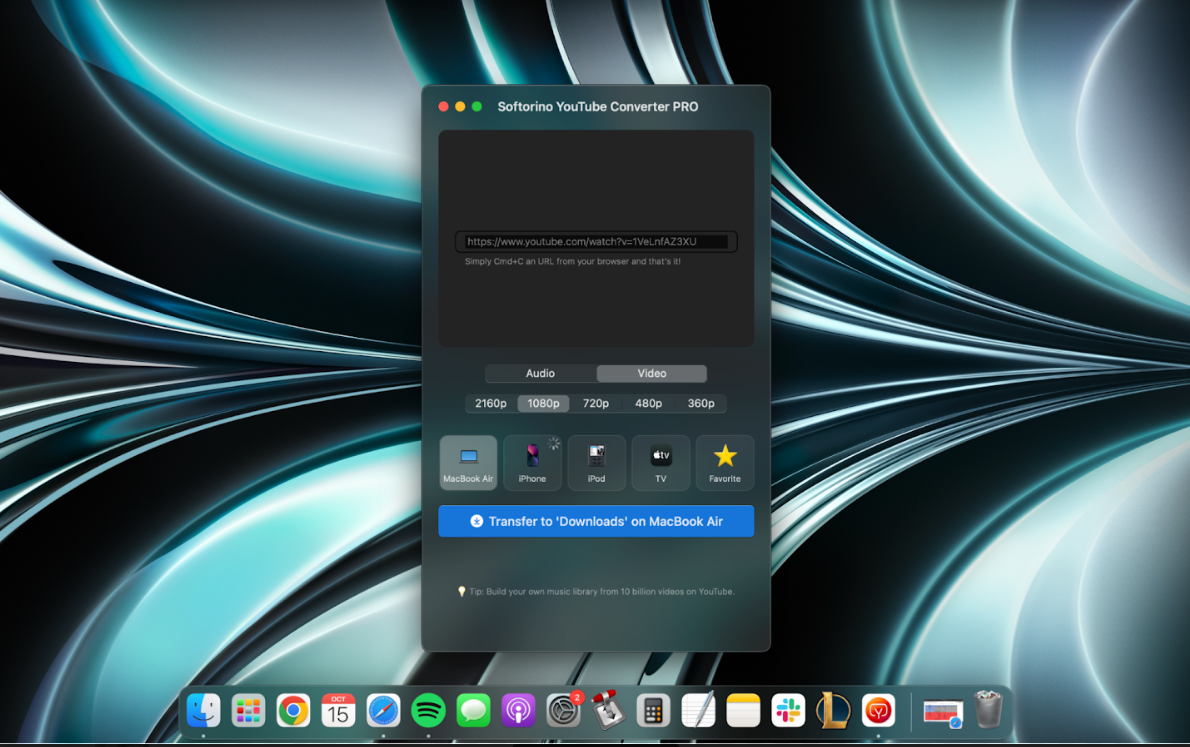
Airy YouTube Downloader, as its name suggests, allows users to download and convert YouTube videos and extract audio files from them for offline and off-platform viewing. The application, created by….

Introduction Admission policies are evolving. Every component changes daily, from how students communicate with colleges to how they handle the entire admissions process. Numerous stakeholders who employ dispersed solutions and….

In the last two decades, software and technology that connects us have become an essential aspect of our existence. Because of the numerous business opportunities and potential future prospects, now….

You might have noticed that the question – What is the best phone case material – is among the most asked questions on the search engines. The reason why people….

The current corporate environment is unstable, and management feels uneasy due to this ongoing instability brought on by outside, uncontrollable causes. Business leaders are challenged because several industries are frozen….

In the digital era, people have become much more connected than ever before. From watching TV to browsing the web, people are turning to the internet to stay connected 24/7…..

To grow your business and reach a wider audience, it’s important to buy Android app installs and gain a competitive edge. As many businesses are coming online, it is crucial….

Introduction Hello, how are you? Today we will give a little introduction to metasploit concepts for a future tutorial that I am planning to upload, well let’s proceed. Developing When….

Hide your IP address and encrypt your data to ensure that your location, identity and activity are never monitored or intercepted. The program builds a secure and encrypted tunnel without….